IDP (OAuth Wrapper) Installation Guide
Step 1: configure organization and project on Trust&Sign side
(Details to be provided by Netheos colleagues)
As a result:
- you have an organization on one of the ekeynox.net servers (https://demo-api.ekeynox.net or https://integration-api.ekeynox.net)
- you have a username of Trust&Sign of your customer's organization (or probably a shared organization)
- you have an API password for that organization
- there are one or several workflows configured in T&S, which can be used in next step in the IDConnect "identity provider" configuration
Step 2: configure the IDConnect Portal
This step covers registering a new Application in the IDConnect back-end and configuring platform settings such as the connection to Trust&Sign for the IDConnect middleware
This step has to be performed by Namirial staff.
Configuration is done on https://esaw-ts-demo.namirial.com/
Login: Namirial account (but user has to be added to the idconnect backend by an admin first)
If it's a newly created organization, fill necessary connection data to connect from IDConnect to Trust&Sign
Go to "Identity Providers" and configure your new identity provider for the specific business case.
The identity provider is the specific configuration which eSignAnyWhere later uses, and which knows by configuration which workflow of Trust&Sign to be used.
Create a new identity provider:
→ note down or copy the client id and client secret to your eSAW configuration!
copy these urls, you will need it in your eSAW configuration.
Complete the wizard and save the just created Identity Provider.
In the processes tab, you see ongoing and completed identification processes (i.e. instances of identification).
Step 3: Configure eSignAnyWhere Identity Provider Configuration
IDConnect Identity Provider hosted by Namirial SpA (TEST environment deployed by Alten)
Prototype version hostet by Namirial SpA, deployed by Alten is working with DEMO environment, therefore on the prototype following redirect URI is configured: https://demo.esignanywhere.net/SawViewer/HttpHandlers/AuthHandler.ashx
Example of a Mapping updates the disposable certificate data and verifies the holder name:
| Parameter | Value | Field Mapping Configuration | Comment | |||
|---|---|---|---|---|---|---|
| Field Property Path | Mode | Data Field | ||||
| Provider Name | e.g. "Netheos Trust&Sign" | Will be shown in eSAW to select the authentication/identification method, and will be shown to the signer in authentication method selection. | ||||
| Client Id | (use the client ID created in step 2. It should have been provided by Namirial sales or presales team) | TEST ClientID for Christoph's Test Org: 09c11f68-2212-4a91-8070-105ba414fc71 | ||||
| Client Secret | (use the client secret created in step 2. It should have been provided by Namirial sales or presales team) | TEST Client Sectet for Christoph: Slack message LR to CB, Tue 26/04/2022 in combination with above's Client ID | ||||
| Scope | openid profile email trustsign | |||||
| Authorization URI | https://esaw-ts-api-demo.namirial.com/identityserver/connect/authorize | |||||
| Token URI | https://esaw-ts-api-demo.namirial.com/identityserver/connect/token | |||||
| Logout URI | ||||||
| JSON Web Token (JWT) Configuration | ||||||
| JWKS URI | https://esaw-ts-api-demo.namirial.com/identityserver/.well-known/openid-configuration/jwks | |||||
| Issuer | https://esaw-ts-api-demo.namirial.com/identityserver | |||||
| Add 'nonce' parameter | Off | |||||
| Validate audience | Off | |||||
| Validate issuer | On | |||||
| Validate lifetime | On | |||||
| Field Mapping | given_name | Validate | Recipient First Name | Note that this is a validation rule to ensure that the signer is the one which the sender defined. When providing an UPDATE rule for the given errror, IDConnect currently returns "Invalid parameter 'firstName' format (Invalid value)": | ||
| Field Mapping | family_name | Validate | Recipient Last Name | Note that this is a validation rule to ensure that the signer is the one which the sender defined | ||
| Field Mapping | identification_type | Update | Disposable Certificate Identification Type | |||
| Field Mapping | document_type | Update | Disposable Certificate Document Type | |||
| Field Mapping | identification_number | Update | Disposable Certificate Identification Number | |||
| Field mapping | (leave out this one for now!!) | Disposable Certificate Phone Number | 20220530: not available in demo process! If left out, it has to be set by the sender in eSAW. | |||
| Field Mapping | issuing_country | Update | Disposable Certificate Document Issuing Country | |||
| Field Mapping | (leave out this one for now!!) | Update | Disposable Certificate Issued By | 20220530: not available in demo process! If left out, it has to be set by the sender in eSAW. Depending on TSP rules, it might be allowed to use a static value which references to Trust&Sign. | ||
| Field Mapping | document_number | Update | Disposable Certificate Document Number | |||
| Field Mapping | identification_country | Update | Disposable Certificate Identification Country | |||
| Field Mapping | (leave out this one for now!!) | Update | Disposable Certificate Document issued On | 20220530: not available in demo process! Depending on TSP rules, it might be allowed to use some artificial value if Trust&Sign process that doesn't return this date is approved. | ||
| Field Mapping | expiry_date | Update | Disposable Certificate Document Expiry Date | |||
Attention:
- Trust&Sign (in this configuration) does NOT offer a phone number. Therefore, the phone number must not be set as UPDATE rule in e.g. another identification configuration which is used as backup option.
- Trust&Sign (in this configuration) does NOT offer a document issuing date.
- Trust&Sign (in this configuration) does NOT offer an issuing authority name ("issued by").
Usage
- Create a new envelope
- Select the document(s) to be signed
- Open the Authentication/Identification section
- Add the OAuth Identification method "Netheos Trust&Sign"
- If indicated, place in the Designer page a signature field and select the signature method "Disposable Certificate".
Screenshots
(passport picture taking)
Backoffice Approval
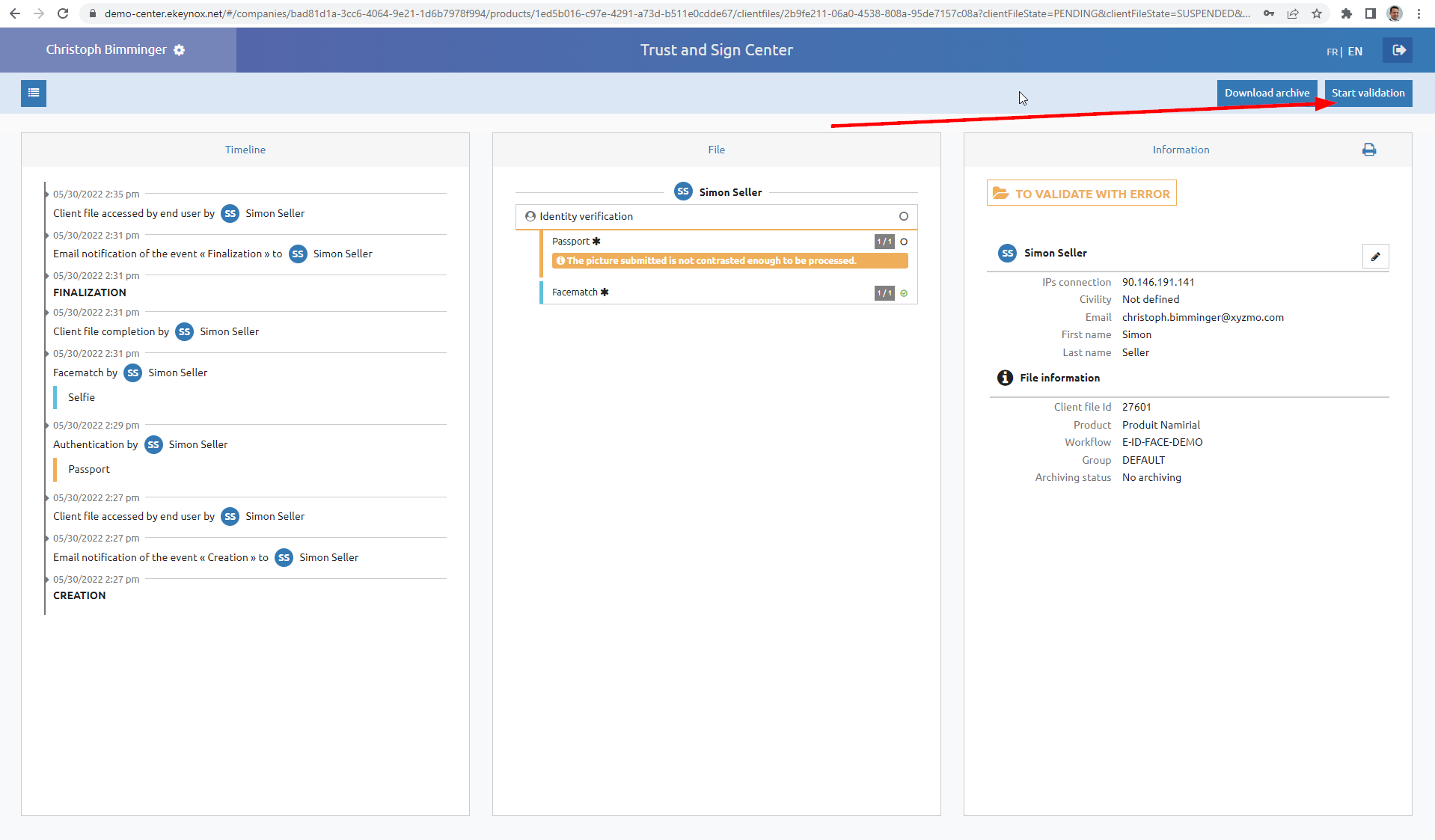
In case the process is one with backoffice approval step, an operator has to log in at https://demo-center.ekeynox.net/ and approve the transaction:
Technical Appendix
Sample JWT returned by the wrapper
{
"iss": "https://esaw-ts-api-demo.namirial.com/identityserver",
"nbf": 1653930619,
"iat": 1653930619,
"exp": 1653930919,
"aud": "09c11f68-2212-4a91-8070-105ba414fc71",
"amr": [
"pwd"
],
"at_hash": "tHwwAcNywwPHqyOX9xzC2A",
"sid": "44874189B9D8A26F1740F37849B0CFC4",
"sub": "91a73a82-341e-4cb7-a3a6-0a7fe9530bdc",
"auth_time": 1653930454,
"idp": "local",
"name": "Simon Seller",
"given_name": "Simon",
"family_name": "Seller",
"email": "christoph.bimminger@xyzmo.com",
"email_verified": [
"true",
true
],
"document_number": "",
"document_type": "PASSPORT",
"identification_number": "",
"identification_type": "PASSPORT",
"identification_country": "",
"issuing_country": "",
"expiry_date": "",
"first_name": "Simon",
"last_name": "Seller",
"preferred_username": "01bd99be-c6cf-44d7-b082-10891c8083f8"
}