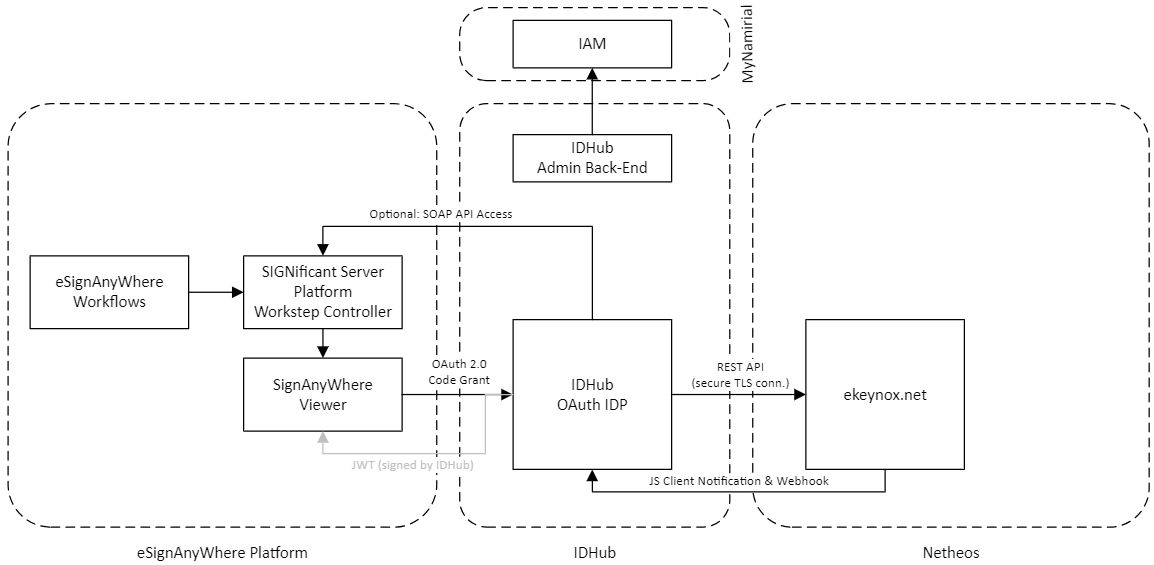
Architecture
To integrate Netheos identification into eSignAnyWhere, several components are in place. All the integration is available out of the box; the below architecture information is just for completeness and probably useful for a better understanding of the below.
Identification and OAuth IDP Configuration Guide
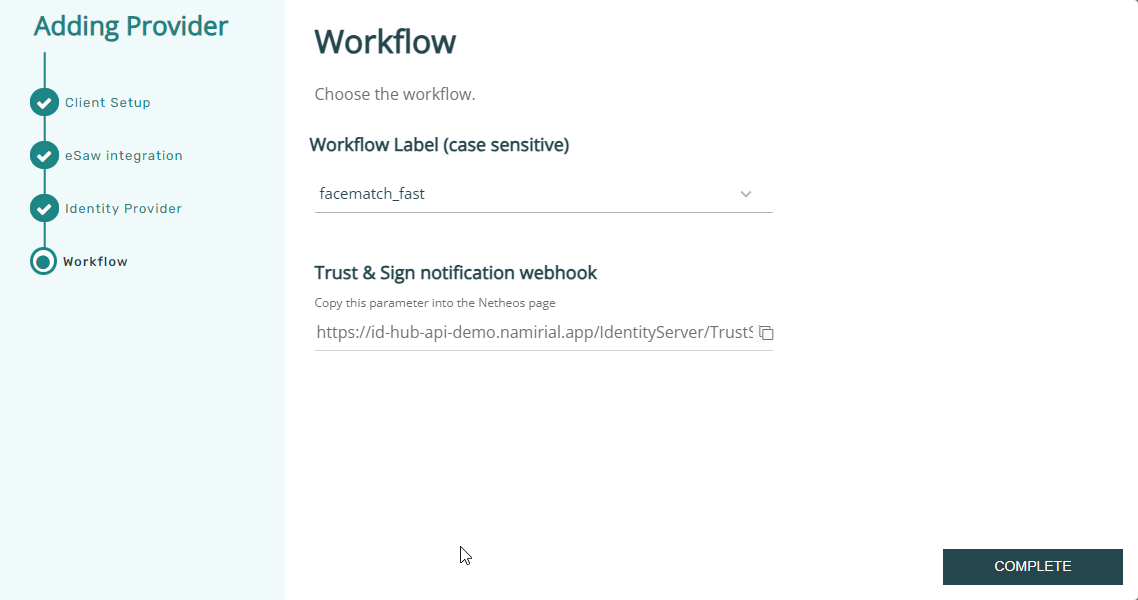
Step 1: configure organization, project and an identification workflow in Netheos product
When configuring a workflow on the Netheos (ekeynox.net) platform, ensure that a proper notification to the integrating component (clientside JS notification as required by IDHub) is part of the workflow.
See Netheos product documentation for detailled instructions.
As a result:
- you have an organization on one of the ekeynox.net servers (https://demo-api.ekeynox.net or https://integration-api.ekeynox.net)
- you have a username of Netheos product of your customer's organization (or probably a shared organization)
- you have an API token for that organization
- there are one or several workflows configured in Netheos, which can be used in next step in the IDHub "identity provider" configuration
Step 2: configure the IDHub OAuth Identity Provider
As shown in the architectural diagram above, IDHub acts as a layer that exposes proprietary API functionality of Netheos through a standardized OAuth compliant interface. If configured, IDHub will also send additional evidence to eSignAnyWhere Platform, which is added as evidence to the Audit Trail.
The configuration step covers registering a new Application in the IDHub administrative back-end and configuring platform settings such as the connection to Netheos (Trust&Sign) for IDHub. This step has to be performed by Namirial staff.
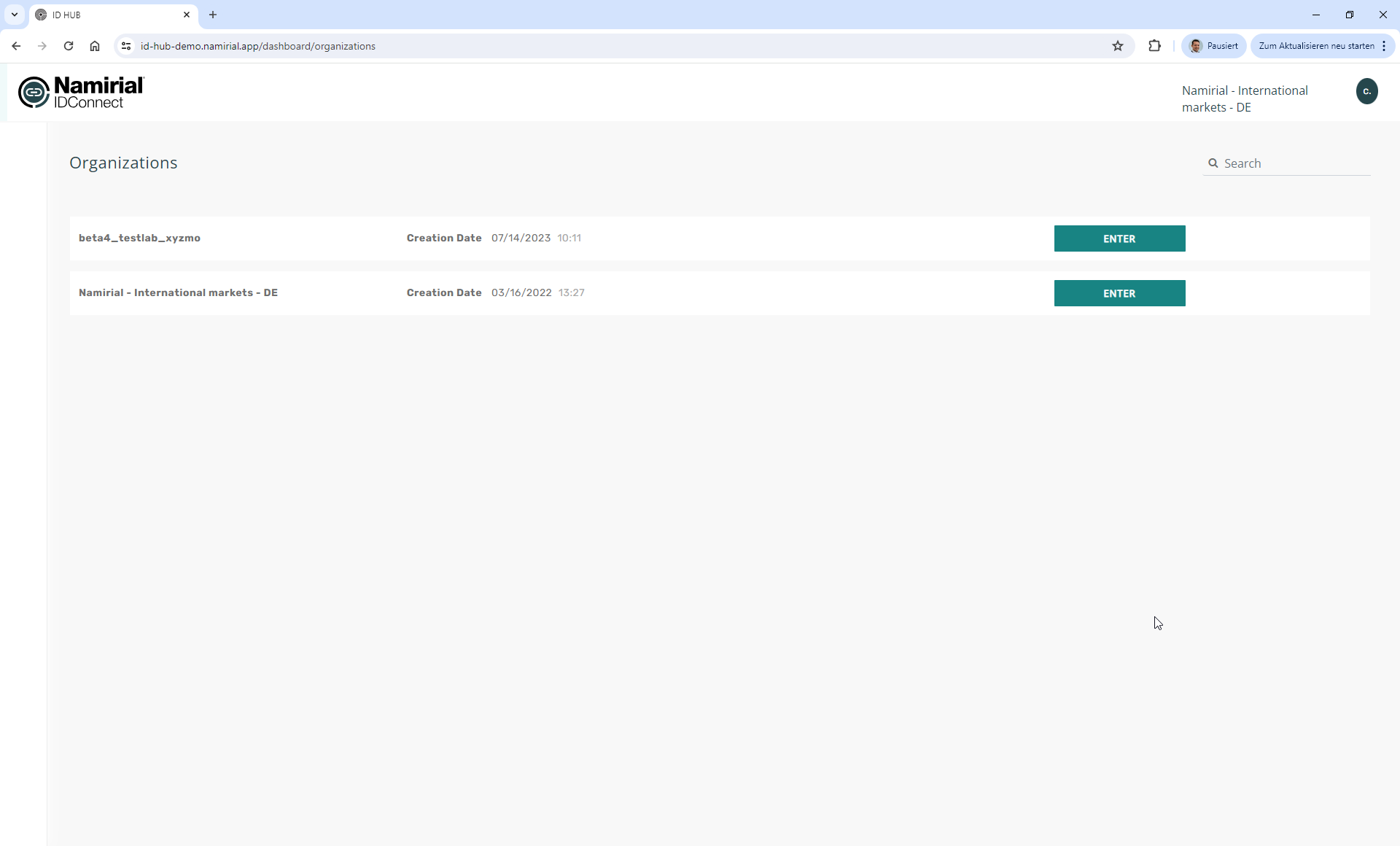
Login to IDHub
| Staging | URL | Comment |
|---|---|---|
| Test/Demo | https://id-hub-demo.namirial.app/ | Authentication requires an account on MyNamirial pre-prod environment (https://auth-preprod.namirial.app/) |
| Production | https://id-hub.namirial.app/ |
The login is performed by using a MyNamirial account of a Namirial staff member. This account must be granted IDHub admin permissions before being able to use an account with these environments.
Tenant/Organization selection
Configuration of Organization Settings
If it's a newly created organization, it will be necessary to fill basic configuration data of the organization.
Basic "Organization Configuration"
the organization name is predefined by the IDHub administrator which created the organization.
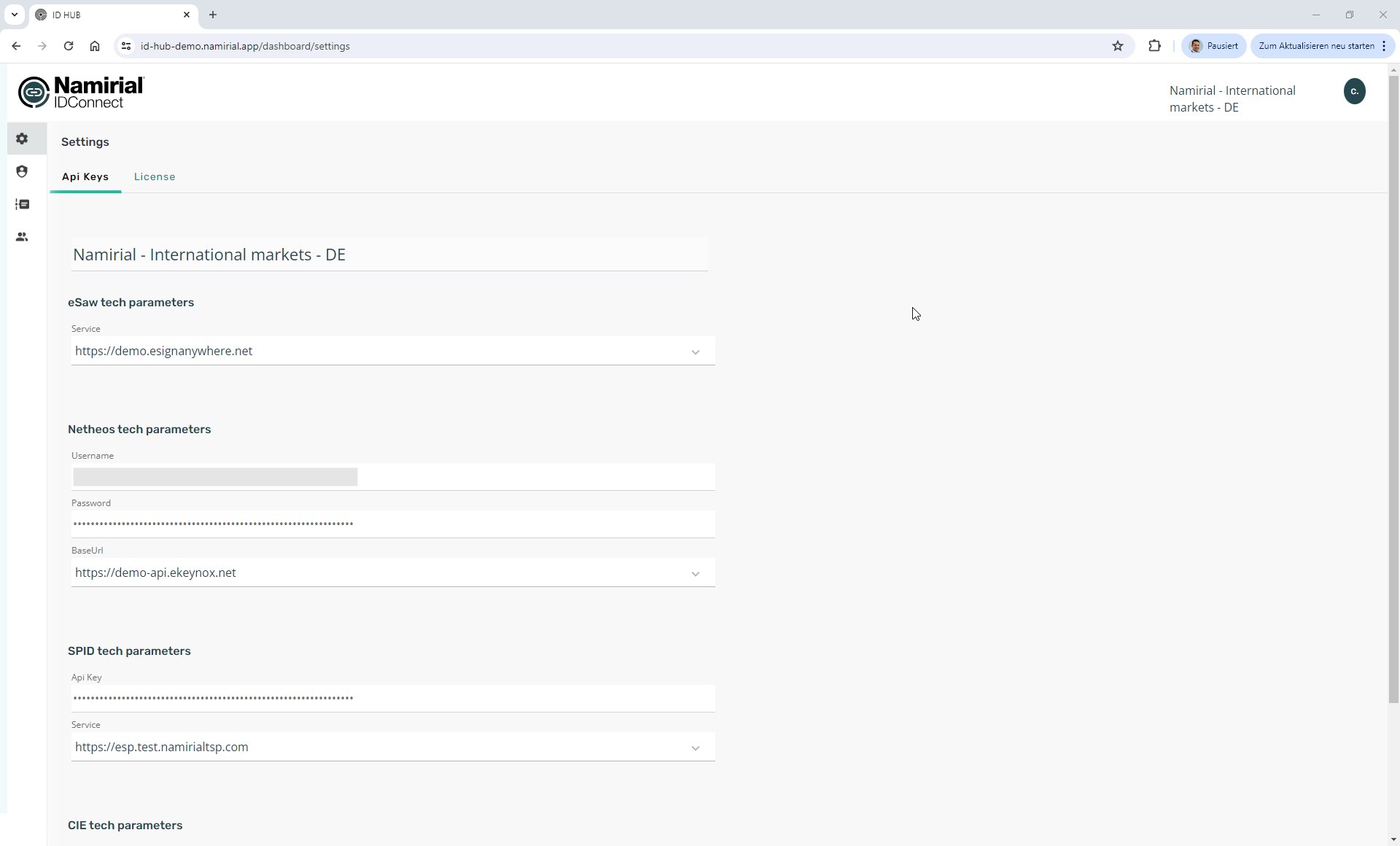
eSAW Tech Parameters
Select to which eSAW instance the IDHub organization will be connected.
The application allows selecting from a predefined list of well-known eSignAnyWhere endpoints. For the well known endpoint, the WorkstepController.Process credentials are already predefined in the IDHub configuration done by the System Administrators.
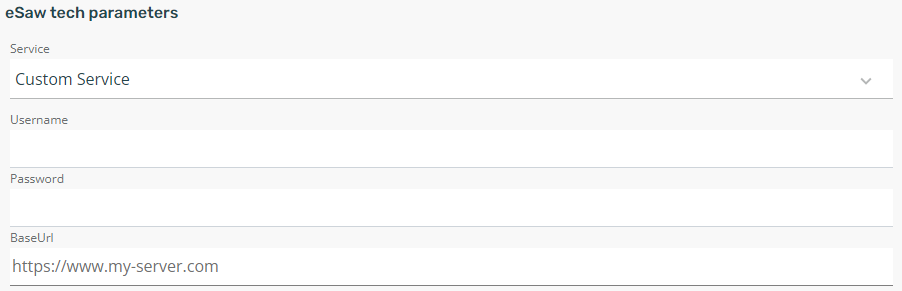
Alternatively, e.g. when connecting with an On-Premise installation of eSignAnyWhere, use the option "Custom Service". In this case, the following additional parameters can be configured:
To use different eSignAnyWhere instances, it is mandatory to have multiple organizations (tenants) in IDHub.
It requires that the target server is installed using Namirial Installation Scripts for eSignAnyWhere, or provides the WorkstepController.Process service at the typical endpoint. Mind to configure only the base URL (without trailing slash). The path and endpoint (/WSCProcess/WorkstepController.Process.asmx) will automatically extended.
Netheos Tech Parameters
Netheos is a user identity verification (IDV) platform developed by Namirial. It offers identification flows such as Facematch Video Fast ("FMV-Fast"), which allow unattended video identification. The configuration is optional and will be necessary only when using IDHub to connect with Netheos.
The settings refer to the API credentials necessary to access the Netheos platform.
The application allows selecting from a predefined list of well-known Netheos endpoints. The URLs are predefined in the IDHub configuration done by the System Administrators.
SPID Tech Parameters
SPID is one the Italian eID options available. The configuration is optional and will be necessary only when using IDHub to connect with SPID infrastructure. It allows identification with SPID issued by Namirial, but also with SPID identities issued by other providers.
These refer to the API credentials necessary to access the Netheos platform.
The application allows selecting from a predefined list of well-known Netheos endpoints. The URLs are predefined in the IDHub configuration done by the System Administrators.
CIE Tech Parameters
CIE is anoner Italian eID options available. The configuration is optional and will be necessary only when using IDHub to connect with CIE infrastructure.
These refer to the API credentials necessary to access the Netheos platform.
The application allows selecting from a predefined list of well-known Netheos endpoints. The URLs are predefined in the IDHub configuration done by the System Administrators.
OAuth Identity Provider Configuration
Open the "Identity Providers" section to configure the identity provider (or in OAuth terminology: the OAuth application).
In this section, configure your new identity provider for the specific business case.
The identity provider is the specific configuration which eSignAnyWhere later uses, and which knows by configuration which workflow of Trust&Sign to be used.
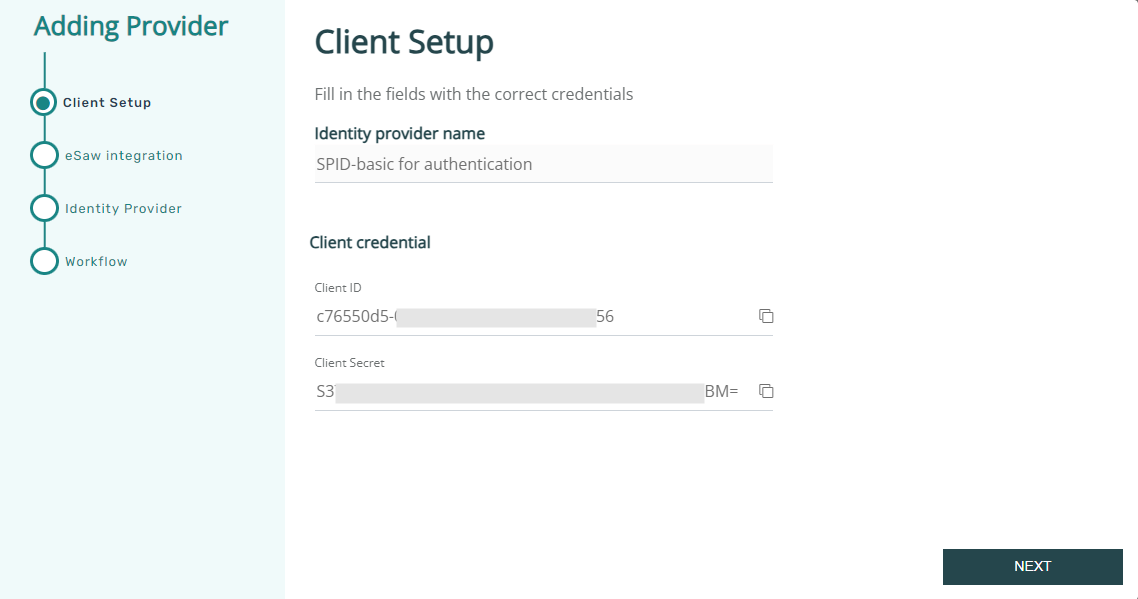
Wizard to create a new identity provider
OAuth Client Application Setup
Important: note down (copy) the client id and client secret to your eSAW configuration! You will need this in a later step. We recommend to store this information in a password manager software of your choice.
If you are used to work with multiple windows in parallel, you can directly create the eSAW-side configuration now and copy/paste the values. Otherwise, if you follow this manual step-by-step, you will need this information later.
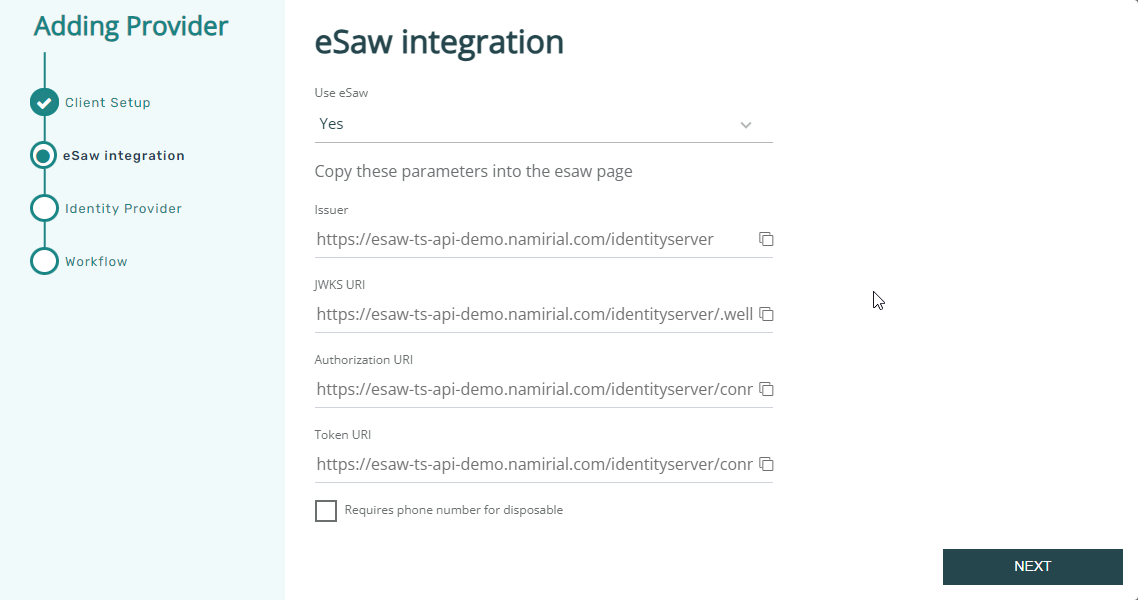
eSAW Parameters
| Parameter | Description |
|---|---|
| Use eSAW | (yes/no): define if the OAuth provider is used with eSignAnyWhere. If declared to be used with eSignAnyWhere, it will fetch data from eSAW and - depending on further configuration - send evidence to the Audit Trail. |
Issuer JWKS URI Authorization URI Token URI | Meant to help configuring the OAuth identity provider in eSignAnyWhere. Copy these urls, you will need it in your eSAW configuration. If you are used to work with multiple windows in parallel, you can directly create the eSAW-side configuration now and copy/paste the values. Otherwise, if you follow this manual step-by-step, you will need this information later. |
Requires phone number for disposables | This checkbox changes the behavior of IDHub. If the phone number was not specified before, IDHub will actively ask the signer to provide his phone number. |
Identity Provider
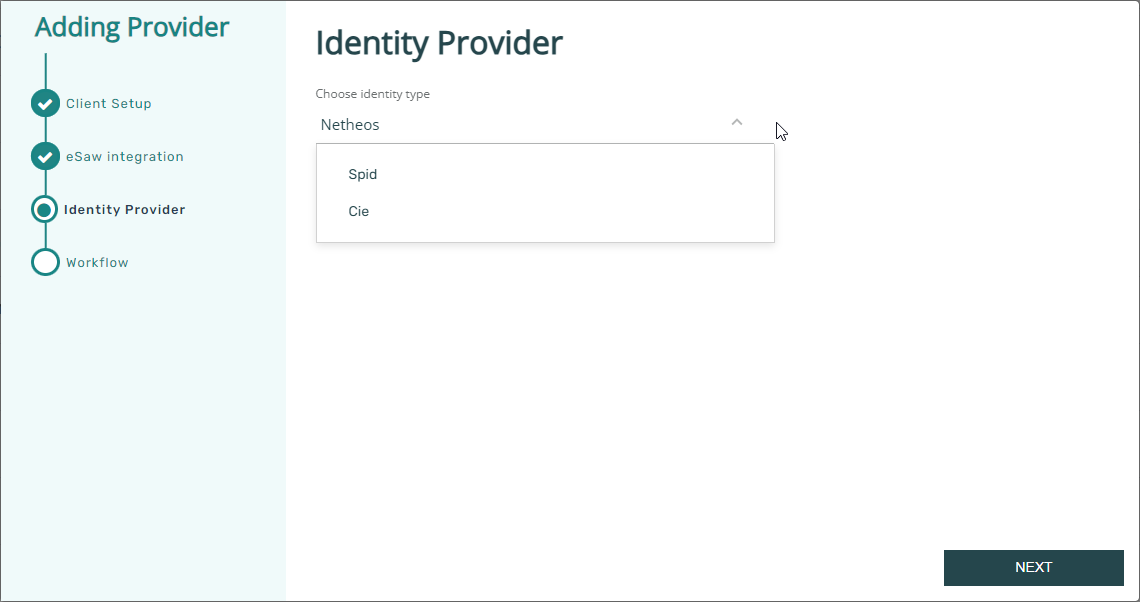
This page requires to select which external identity provider to be offered through an OAuth interface for this specific identity provider configuration (= OAuth application).
For Netheos identification, choose the value "Netheos".
If you want to allow using different identification methods, it will be necessary to set up multiple Identity Providers within your IDHub organization and configure all of them as Identity Providers in eSignAnyWhere.
Complete the wizard and save the just created Identity Provider.
In the processes tab, you see ongoing and completed identification processes (i.e. instances of identification).
Step 3: Configure eSignAnyWhere Identity Provider Configuration
IDHub Identity Provider (Test)
eSignAnyWhere test and demo environments (including demo.esignanywhere.net) are connected to the The IDHub test environment.
Example of a Mapping updates the disposable certificate data and verifies the holder name:
| Parameter | Value | Field Mapping Configuration | Comment | |||
|---|---|---|---|---|---|---|
| Field Property Path | Mode | Data Field | ||||
| Provider Name | e.g. "Netheos Facematch" | Will be shown in eSAW to select the authentication/identification method, and will be shown to the signer in authentication method selection. | ||||
| Client Id | (use the client ID created in step 2. It should have been provided by Namirial sales or presales team) | TEST ClientID for Christoph's Test Org: 09c11f68-2212-4a91-8070-105ba414fc71 | ||||
| Client Secret | (use the client secret created in step 2. It should have been provided by Namirial sales or presales team) | TEST Client Sectet for Christoph: Slack message LR to CB, Tue 26/04/2022 in combination with above's Client ID | ||||
| Scope | openid profile email trustsign | |||||
| Authorization URI | https://esaw-ts-api-demo.namirial.com/identityserver/connect/authorize | |||||
| Token URI | https://esaw-ts-api-demo.namirial.com/identityserver/connect/token | |||||
| Logout URI | ||||||
| JSON Web Token (JWT) Configuration | ||||||
| JWKS URI | https://esaw-ts-api-demo.namirial.com/identityserver/.well-known/openid-configuration/jwks | |||||
| Issuer | https://esaw-ts-api-demo.namirial.com/identityserver | |||||
| Add 'nonce' parameter | Off | |||||
| Validate audience | Off | |||||
| Validate issuer | On | |||||
| Validate lifetime | On | |||||
| Field Mapping | given_name | Validate | Recipient First Name | Note that this is a validation rule to ensure that the signer is the one which the sender defined. When providing an UPDATE rule for the given field, IDHub currently returns "Invalid parameter 'firstName' format (Invalid value)" | ||
| Field Mapping | family_name | Validate | Recipient Last Name | Note that this is a validation rule to ensure that the signer is the one which the sender defined | ||
| Field Mapping | identification_type | Update | Disposable Certificate Identification Type | |||
| Field Mapping | document_type | Update | Disposable Certificate Document Type | |||
| Field Mapping | identification_number | Update | Disposable Certificate Identification Number | |||
| Field mapping | phone_number | Disposable Certificate Phone Number | ||||
| Field Mapping | issuing_country | Update | Disposable Certificate Document Issuing Country | |||
| Field Mapping | issued_by | Update | Disposable Certificate Issued By | |||
| Field Mapping | document_number | Update | Disposable Certificate Document Number | |||
| Field Mapping | identification_country | Update | Disposable Certificate Identification Country | |||
| Field Mapping | issued_on | Update | Disposable Certificate Document issued On | |||
| Field Mapping | expiry_date | Update | Disposable Certificate Document Expiry Date | |||
Attention:
- Netheos (in this configuration) does NOT offer a phone number. Therefore, the checkbox in IDHub must be enabled to ask for the phone number. Otherwise it cannot be set as UPDATE rule.
Usage
- Create a new envelope
- Select the document(s) to be signed
- Open the Authentication/Identification section
- Add the OAuth Identification method "Netheos Trust&Sign"
- If indicated, place in the Designer page a signature field and select the signature method "Disposable Certificate".
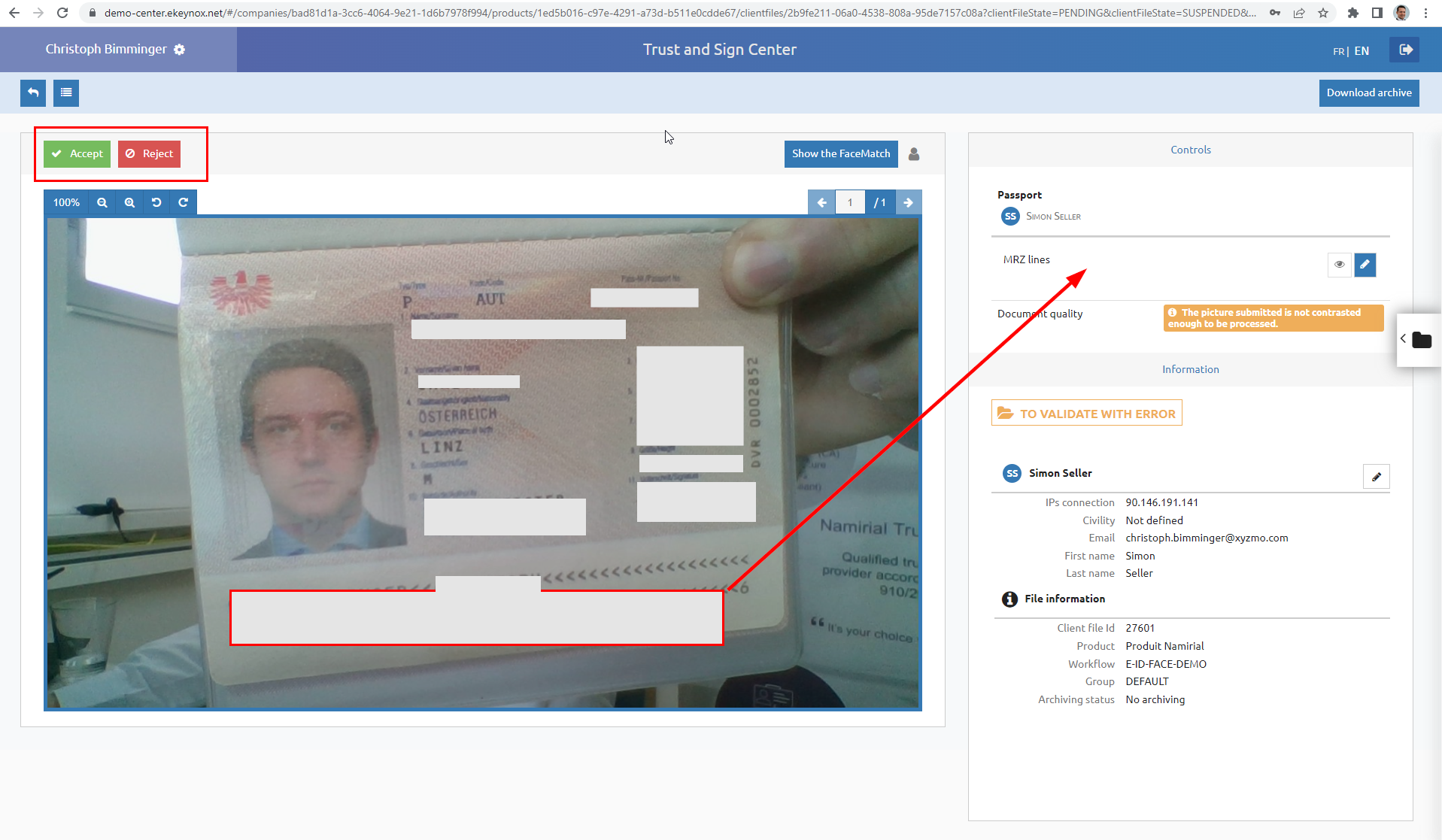
Backoffice Approval
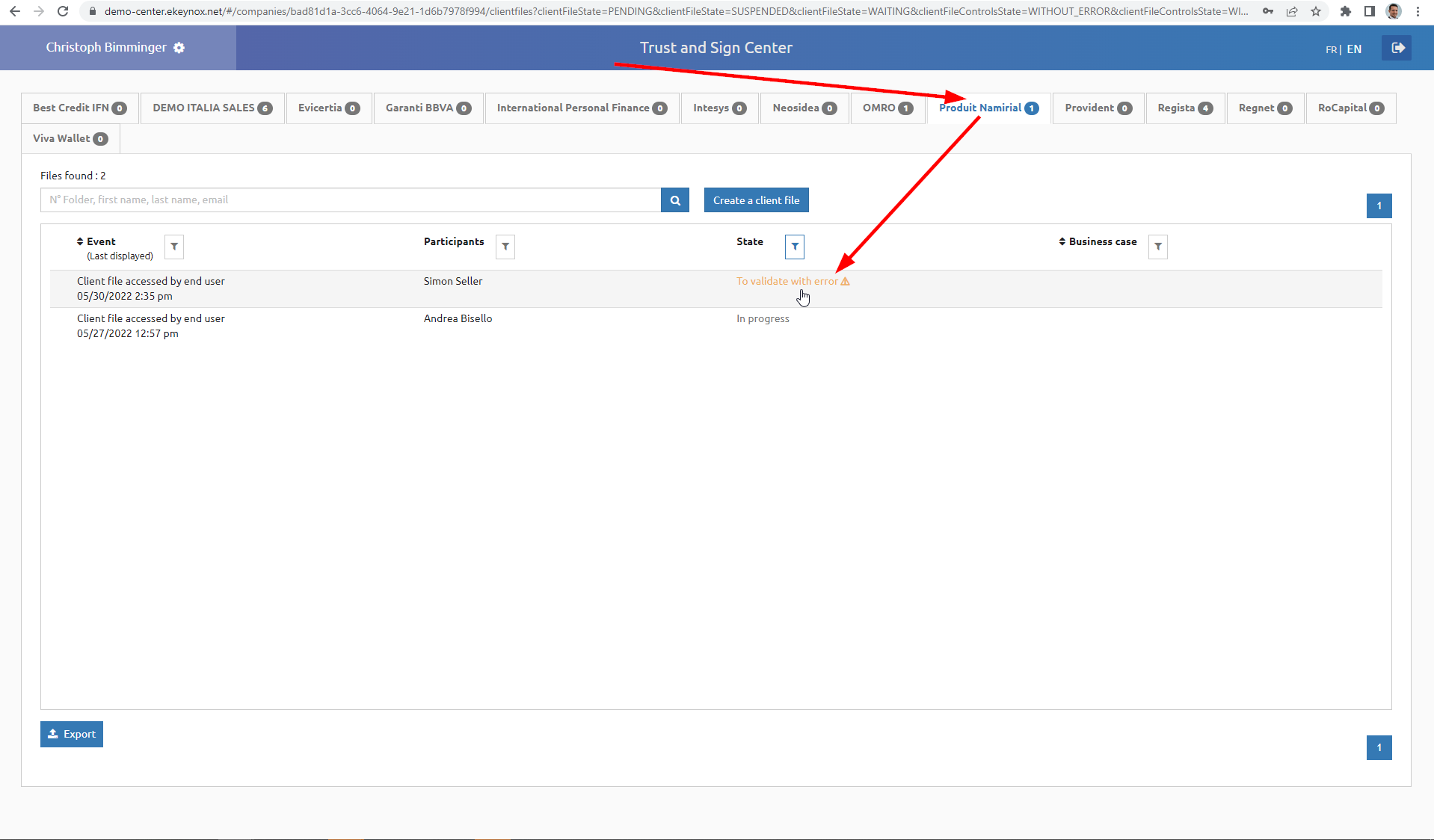
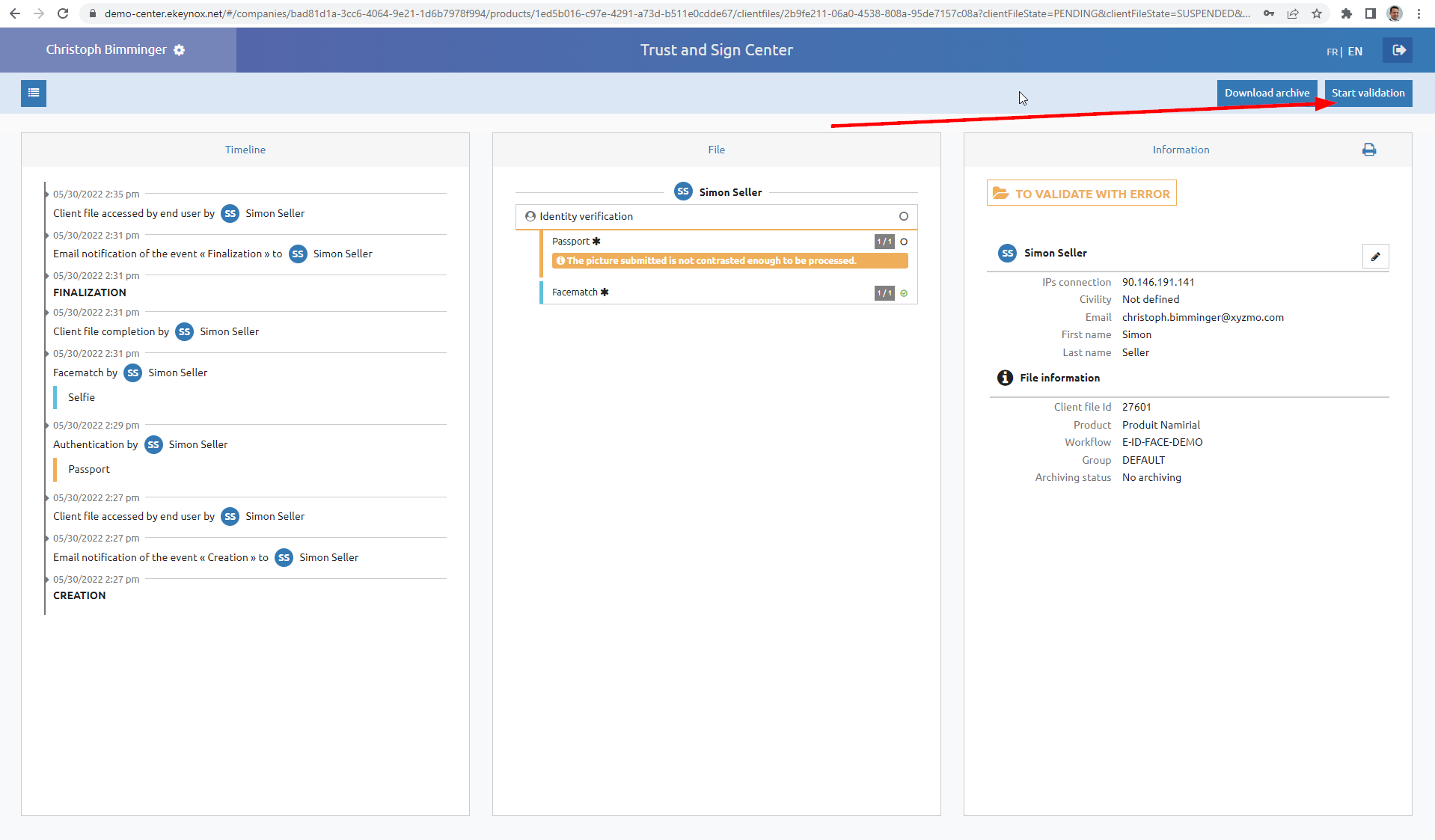
In case the process is one with backoffice approval step, an operator has to log in at Netheos agent portal and approve the transaction.
| Staging | URL |
|---|---|
| Demo/Test | https://demo-center.ekeynox.net/ |
| Production | communicated during project |
Technical Appendix
Sample JWT returned by the wrapper
{
"iss": "https://<url>/identityserver",
"nbf": 1653930619,
"iat": 1653930619,
"exp": 1653930919,
"aud": "09c11f68-2212-4a91-8070-105ba414fc71",
"amr": [
"pwd"
],
"at_hash": "tHwwAcNywwPHqyOX9xzC2A",
"sid": "44874189B9D8A26F1740F37849B0CFC4",
"sub": "91a73a82-341e-4cb7-a3a6-0a7fe9530bdc",
"auth_time": 1653930454,
"idp": "local",
"name": "Simon Seller",
"given_name": "Simon",
"family_name": "Seller",
"email": "xxxxxx.xxxxxxxxx@example.com",
"email_verified": [
"true",
true
],
"document_number": "",
"document_type": "PASSPORT",
"identification_number": "",
"identification_type": "PASSPORT",
"identification_country": "",
"issuing_country": "",
"expiry_date": "",
"first_name": "Simon",
"last_name": "Seller",
"preferred_username": "01bd99be-c6cf-44d7-b082-10891c8083f8"
}
Keywords
Trust&Sign, Facematch, FMV Photo, FMV Fast